How Phishing Works in 2025: The Modern Kill Chain (Email, QR, Deepfakes, and SaaS)
TL;DR
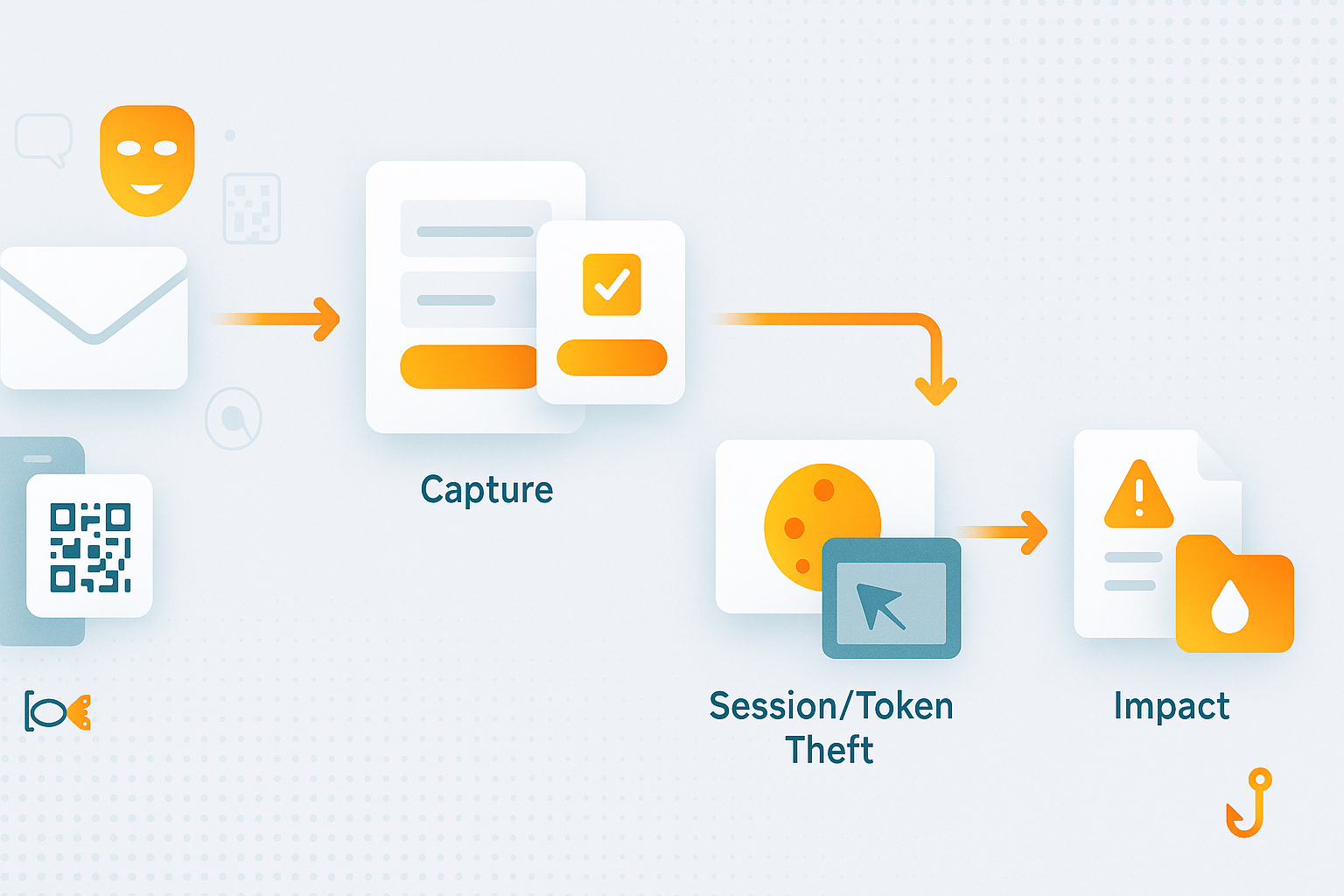
- Lure → Capture → Session/Token theft → Lateral movement → Impact
- Identity + session protection is everything—and the fastest path to durable resilience is frequent, realistic practice that builds instinct.
Intro
If you’re wondering how phishing works in 2025, here’s the honest answer: attackers rarely stop at passwords — they want your session. And if they can’t get you by email, they’ll try a QR code on your phone, a slick SaaS consent screen, or even a deepfaked video call with your “CFO.” Fun (for them).
Below is the modern kill chain most incidents follow—plus where AutoPhish makes you much harder to fool.
1) The Lure: email, QR, and scarily convincing “humans”
Phishing still arrives by email, but URLs are the star. Proofpoint’s latest Human Factor 2025 research shows URLs are used around four times more than attachments in malicious emails—and 4.2 million QR-code (quishing) threats were flagged in just the first half of 2025 (blog overview, Vol. 2 report page).
Then there’s the human layer: deepfake video/voice. The Arup case—~$25M lost after a deepfaked group call—shows how social engineering now looks like a perfectly normal meeting invite (Guardian, World Economic Forum). Policies that require secondary verification beat “vibes” every time.
Want a field guide to spot the tricks inside a single message? Start with The Anatomy of a Modern Phishing Email on our blog.
2) Capture: credentials or consent—both open the door
Attackers don’t always ask for your password. Increasingly, they present a legit-looking SaaS/OAuth consent screen (“Allow this app to read your mail?”). If you click Allow, they gain durable API access—no password needed. Microsoft’s guidance on illicit consent grants explains detection and remediation (Microsoft Learn Microsoft Learn 2; also see the app-consent incident response playbook).
Old-school credential harvesters still work, often hosted behind reputable services (forms/storage/view-only files) to dodge filters. Proofpoint’s Human Factor series and Microsoft’s threat posts highlight the shift toward URL-centric delivery (Proofpoint, Microsoft).
3) Session/Token theft: bypassing MFA with a tiny man-in-the-middle
Here’s the 2025 twist: Adversary-in-the-Middle (AiTM) toolkits sit between you and Microsoft/Google, proxy the login, and steal your session cookie after you successfully pass MFA. The attacker then replays that cookie and walks right in—no password, no second factor. See Microsoft’s analyses and playbooks, plus Proofpoint and Talos reporting (MSFT Security Blog; see also:
- Cisco Talos IR:ry-point-to-further-financial-fraud/),
- Multi‑stage AiTM,
- Session‑cookie theft alert playbook
- Proofpoint on AiTM
- Talos IR Q2 2025.
4) Lateral movement: once inside, attackers get comfy
With mailbox or token access, attackers set inbox rules, register malicious OAuth apps, and pivot to perform BEC—sometimes for weeks before anyone notices (see Microsoft’s guidance on session-cookie theft alerts: learn.microsoft.com). For real-world color (and quick guardrails), see [10 Wild Phishing (and Phish-Adjacent) Stories from 2024–2025](https://autophish.io/blog/10-wild-phishing-and-phish-adjacent-stories-from-2024-2025-including-important-lessons-learned from-2024-2025-including-important-lessons-learned).
5) What actually stops this? (Practical controls)
- Phishing-resistant MFA (passkeys/FIDO2) and limiting weak fallbacks (SMS/voice codes). CISA and NIST‑aligned guidance: CISA success story (USDA), CISA HISG on passkeys, and the Phishing‑Resistant Authenticator Playbook (IDManagement.gov). For a plain‑English explainer, see WIRED’s overview of how passkeys work.
- Consent governance: block risky OAuth app consent, require admin approval, and educate users about what an app is asking for (Microsoft Learn.
- Anti‑AiTM controls: conditional access with token binding where possible, vigilant revocation of sessions, and alerts on unusual inbox rules (MSFT Token Theft Playbookicrosoft.com/en-us/security/operations/token-theft-playbook)).
- User behavior: treat QR codes like links; don’t scan from unsolicited messages. Proofpoint’s 2025 data shows quishing is mainstream now (Proofpoint blog).
Where AutoPhish makes a measurable difference
AutoPhish is designed around those exact failure points (and it’s EU/GDPR‑friendly by design):
- Role‑aware realism. We generate ever‑fresh lures per role and industry (finance, HR, execs)—covering emails, QR campaigns, and SaaS‑consent prompts. That builds instinct against the attacks people actually face. Learn how we do it in Phishing Simulations‑as‑a‑Service Explained.
- Kill‑chain‑aware simulations. We don’t stop at a click—we teach what a consent screen looks like, why it’s risky, and how to respond (see also our Anatomy of a Modern Phishing Email guide).
- Just‑in‑time training + clear reports you can take to audits (NIS2/ISO‑friendly). If you’re weighing formats, compare Automated vs. Manual Campaigns.
- Employee‑friendly & GDPR‑smart. Options for anonymization/pseudonymization, short retention, and works‑council‑compatible guardrails—because culture and compliance matter. Details: Privacy‑Friendly Phishing Training.
Curious about open-source vs. SaaS trade‑offs? We’ve compared them in Open‑Source Tools vs. Managed Solutions.
FAQ: How phishing works
Can a phishing link install malware?
Yes. A link can trigger a drive‑by download or lead to a site that drops malware—or it can simply steal your credentials. Keep software patched, use reputable endpoint protection, and avoid opening links/attachments from unknowns (Emsisoft explainer, Kaspersky).
Can phishing be done by phone?
Absolutely. Vishing (voice) and smishing (SMS) are mainstream—often augmented with AI voice cloning. Verify through a known channel before acting (definitions from the FBI and FCC).
What is “quishing”?
QR‑code phishing: a message/poster contains a QR code that sends you to a malicious site—often on your phone, away from enterprise protections. Treat QR codes like links; don’t scan from unsolicited messages (see Proofpoint’s 2025 data on QR threats: overview).
Does MFA stop all phishing?
MFA is essential, but AiTM can steal the session cookie after MFA. Prefer phishing‑resistant MFA (passkeys/FIDO2) and disable weak fallbacks (SMS/voice) where you can ([MSFT on AiTM](https://www.microsoft.com/en-us/security/blog/2022/07/12/from-cookie-theft-to-bec-attackers-use-aitm-phishing-sites-as-entry-point-to-further-financial-fraud/; see also https://www.microsoft.com/en-us/security/blog/2023/06/08/detecting-and-mitigating-a-multi-stage-aitm-phishing-and-bec-campaign/; Cisco Talos IR: https://blog.talosintelligence.com/ir-trends-q2-2025/)); CISA playbooks.
What’s OAuth consent phishing, in one sentence?
A malicious app asks for permission to your data; if you click Allow, it keeps API access until consent is revoked—even without your password (Microsoft Learn).
Want this explained to your whole team—with hands‑on practice? Launch a monthly, role‑aware program in minutes with AutoPhish. Make your people the firewall.