Blog

GoPhish alternative in 2026: safer phishing simulations without running an attack toolkit
Commercial investigation / solution selection for phishing simulations and security awareness training

Phishing Simulation Reporting: 12 Features Security Teams Should Compare (Dashboards, Metrics, and Audit Evidence)

SPF, DKIM, DMARC & Domain Permutations: The Email Security Basics Attackers Exploit
Email is still the easiest way into most companies—because attackers don’t need to hack servers if they can convincingly impersonate a trusted sender. In real-world breaches, the “human element” shows up again and again, and phishing remains a dominant initial access path.
Phishing Trends in 2026: What’s Really Changing (and What Isn’t)
See the top phishing trends for 2026—AI deepfakes, mobile/QR, SaaS consent abuse, and trust infrastructure. Practical defenses for SMEs.
Phishing on Mobile: SMS, WhatsApp & QR - What Policies SMEs Actually Need
Mobile is now the frontline of phishing. Staff approve MFA prompts on their phones, scan QR codes at the office door, and link business chats to desktop via QR. Attackers follow that trail. This guide gives SMEs copy-pasteable policy language and quick controls you can deploy this week, grounded in recent advisories and what we see in the field.
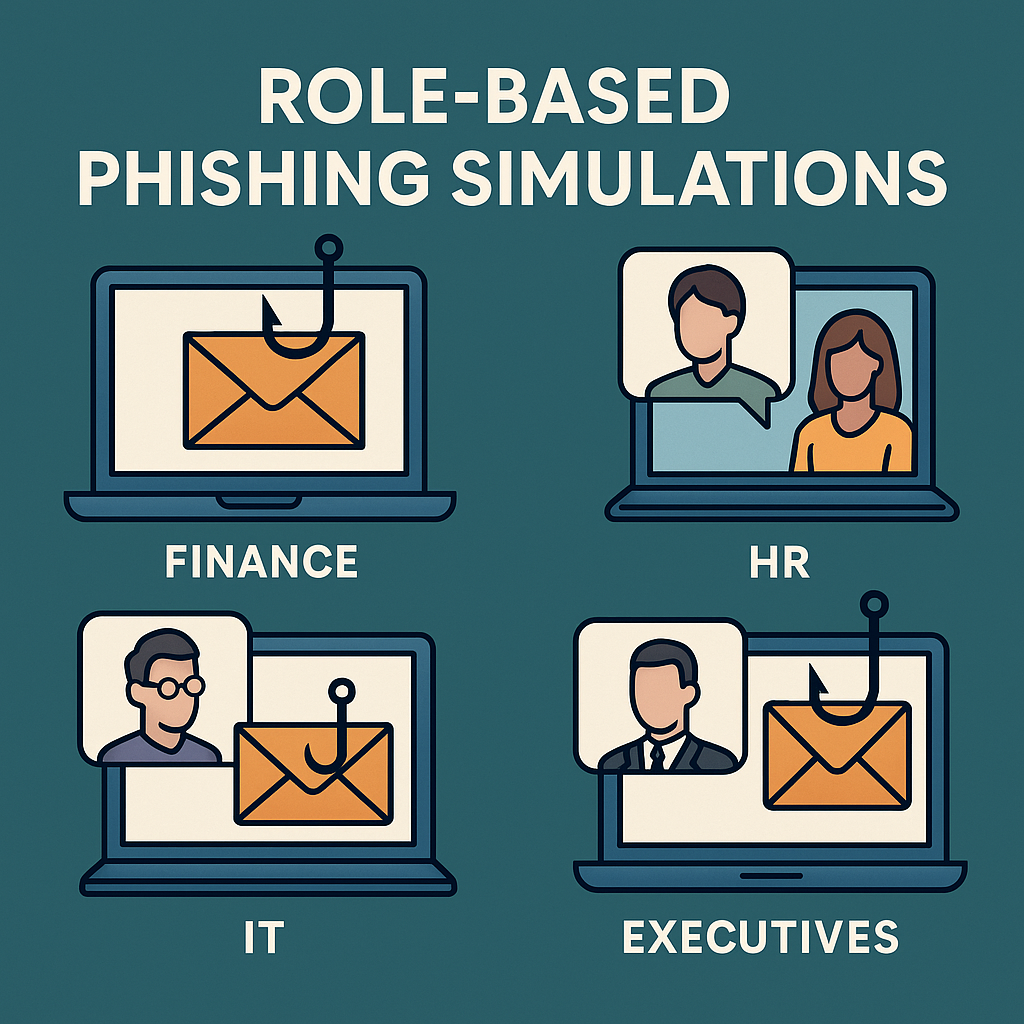
Role-Based Phishing Simulations: Finance, HR, IT & Execs — Scenarios, Guardrails, and Metrics
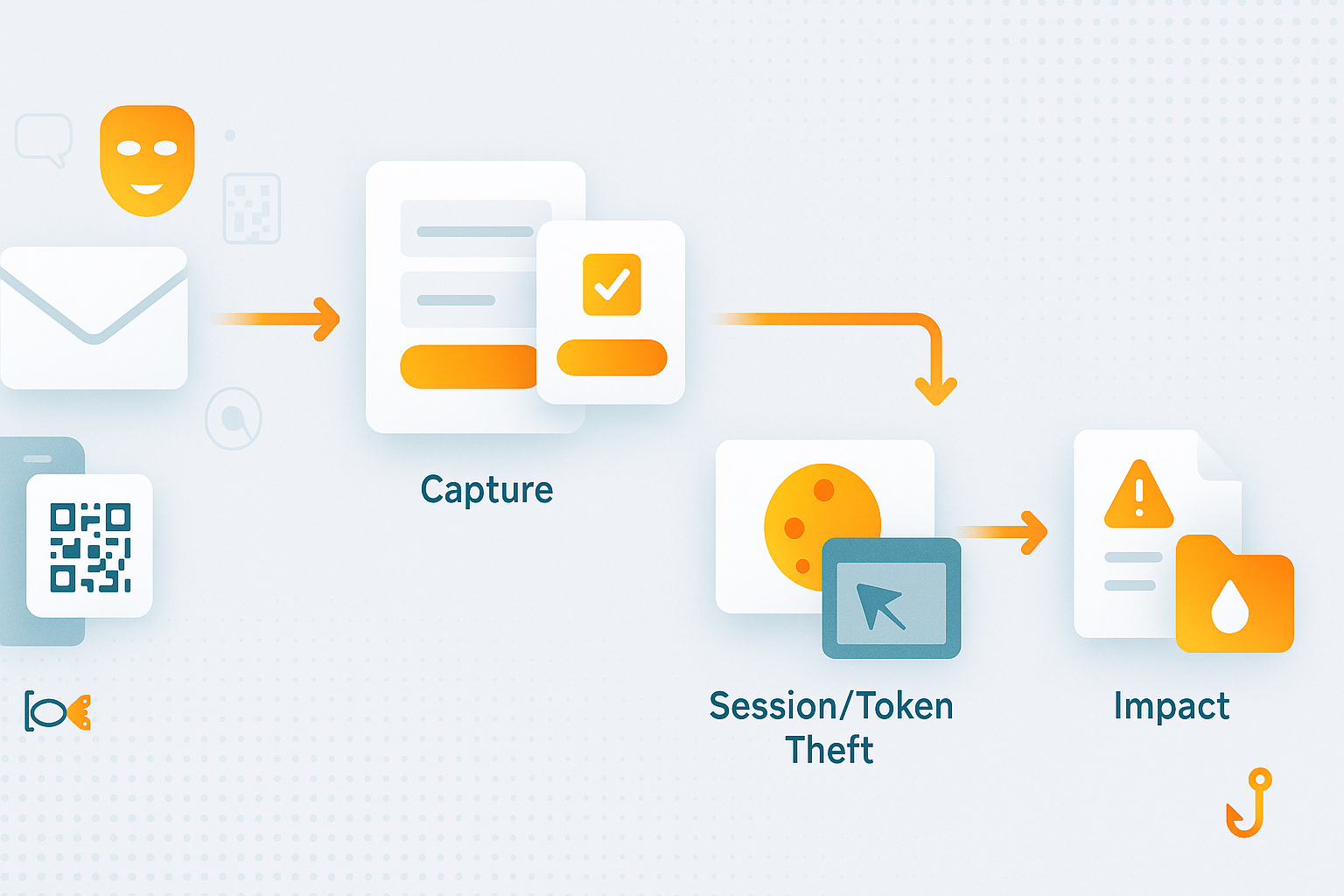
How Phishing Works in 2025: The Modern Kill Chain (Email, QR, Deepfakes, and SaaS)

10 Wild Phishing (and Phish-Adjacent) Stories from 2024–2025 – including important Lessons Learned

Privacy-Friendly Phishing Training: Works Councils, Consent, and GDPR Essentials
How to design a program that’s effective *and* employee-friendly: anonymization options, data retention, and clear notices
Automated Phishing Testing vs. Manual Campaigns: Which Is Best for Your Business?
Pronto a rafforzare le tue difese?
Iscriviti e lancia la tua prima simulazione phishing in pochi minuti.